Table of Contents
- Introduction
- How to do packet capture on remote machine over ssh from Windows machine
- Things needed on Linux machine side : SSH server
- Things needed on the Windows machine side : SSH client
- How to run remote packet capture as a sudo user using ssh from windows cmd
- how to do ‘-S’ option way in the same command
- How to setup password less entry for Sudo user while using the same command on Windows cmd
- How to run remote packet capture using the same command from windows cmd as a root user
- How to do packet capture on a remote machine over ssh from linux machine
- Things needed on Linux machine side : SSH server
- Things needed on the Linux machine side : SSH client
- How to run remote packet capture as a sudo user while using ssh command from a bash terminal
- How to do ‘-S’ option way in the same command
- How to setup password less entry for Sudo user while using the same command on bash terminal
- How to run remote packet capture using the same command from bash terminal as a root user
Introduction
Are you wondering how to capture the packets on a remote linux machine and stream it over the ssh to the local machine to view it in wireshark ? This article will help you understand how to streams packet captures from linux machine to a windows or another linux machine / mac over ssh
How to do packet capture on remote machine over ssh from Windows machine
In most of the linux systems ssh server is enabled by default. Windows power shell or the command prompt comes with the ssh client instance pre-installed nowadays, using that we will be able to access a linux machine over ssh. SSH as a protocol supports many features like X forwarding , streaming of the live packet captures , tunneling , SCP , etc . In this section we will see in detail with examples on how to perform remote streaming of the packet captures over ssh and view it on wireshark on a windows machine
Things needed on Linux machine side : SSH server
We need to make sure whether the ssh server instance is configured on a linux machine.
Usernames with full privilege to run tcpdump on a linux machine to be configured
Things needed on the Windows machine side : SSH client
Wireshark needs to be installed and we must know the path of the install directory , it is easier to execute the plink command on the location of the wireshark package inorder to avoid reference the path of the package in the command execution.
Open a command prompt which supports the plink command on a windows machine
In order to view all the options supported by the plink we can use the help option
C:\Program Files\Wireshark>plink --helpHow to run remote packet capture as a sudo user using ssh from windows cmd
Make sure you are on the wireshark install location before running the following command
We can see that the following command errored out with a message that the sudo user either needs to use option -S to enter the sudo password while prompted or we need to set up the askpass helper.
C:\Program Files\Wireshark> plink -batch -ssh -pw password@123 user1@192.168.44.151 "sudo tcpdump -i ens33 -s 0 -w - -U " | .\wireshark.exe -k -i -
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
Lets see ways on fixing this issue
how to do ‘-S’ option way in the same command
Following command with -S option will prompt asking for password while execution . This password is part of the credential we use to execute commands as a sudo user. Once the password is entered after the prompt , we will see the tcpdump command will be started and wireshark will also run on the windows machine
C:\Program Files\Wireshark> plink -batch -ssh -pw password@123 user1@192.168.44.151 "sudo -S tcpdump -i ens33 -s 0 -w - -U " | .\wireshark.exe -k -i -
[sudo] password for user1:
tcpdump: listening on ens33, link-type EN10MB (Ethernet), snapshot length 262144 bytes
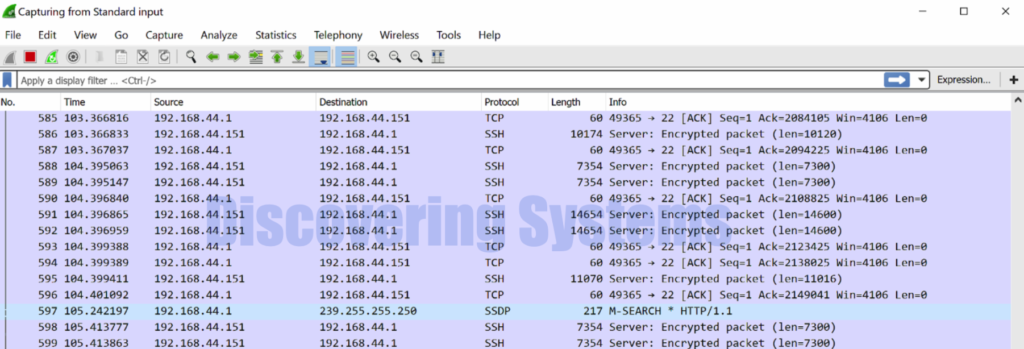
How to setup password less entry for Sudo user while using the same command on Windows cmd
We can edit the sudoers file in a way that it asks for no password while executing the commands as a sudo user. Following is a example on how to make this happen
You can either directly edit the sudoers file or use the visudo to perform the edit , editing through visudo is the recommended way
vi /etc/sudoersOr
visudoAnd add below content and save it
user1 ALL=(ALL) NOPASSWD: ALL
%sudo ALL=(ALL:ALL) NOPASSWD:ALL
From now on we will be able to execute commands as a sudo user without password being asked on a linux machine. Now the below worked without throwing an error even without using the ‘-S’ option
C:\Program Files\Wireshark> plink -batch -ssh -pw password@123 user1@192.168.44.151 "sudo tcpdump -i ens33 -s 0 -w - -U " | .\wireshark.exe -k -i -
tcpdump: listening on ens33, link-type EN10MB (Ethernet), snapshot length 262144 bytes
How to run remote packet capture using the same command from windows cmd as a root user
While running the similar command as a root user , it is going to be very easy as a root user because of full privilege.
C:\Program Files\Wireshark> plink -batch -ssh -pw password@123 root@192.168.44.151 "sudo tcpdump -i ens33 -s 0 -w - -U " | .\wireshark.exe -k -i -
tcpdump: listening on ens33, link-type EN10MB (Ethernet), snapshot length 262144 bytes
How to do packet capture on a remote machine over ssh from linux machine
Now lets try the same on a linux machine installed with the wireshark GUI and Cli package
Things needed on Linux machine side : SSH server
We need to make sure whether the ssh server instance is configured on a linux machine.
Usernames with full privilege to run tcpdump on a linux machine to be configured
Things needed on the Linux machine side : SSH client
Wireshark GUI and Cli package needs to be installed
How to run remote packet capture as a sudo user while using ssh command from a bash terminal
We can see that the following command errored out with a message that the sudo user either needs to use option -S to enter the sudo password while prompted or we need to set up the askpass helper.
[root@discoveringsystems-centos /]# ssh user1@192.168.94.100 "sudo tcpdump -i ens33 -s 0 -w - -U" | wireshark -k -i -
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
Lets see ways on fixing this issue
How to do ‘-S’ option way in the same command
Following command with -S option will prompt asking for password while execution . This password is part of the credential we use to execute commands as a sudo user. Once the password is entered after the prompt , we will see the tcpdump command will be started and wireshark will also run on the windows machine
[root@discoveringsystems-centos /]# ssh user1@192.168.94.100 "sudo -S tcpdump -i ens33 -s 0 -w - -U" | wireshark -k -i -
[sudo] password for user1:
tcpdump: listening on ens33, link-type EN10MB (Ethernet), snapshot length 262144 bytes
How to setup password less entry for Sudo user while using the same command on bash terminal
We can edit the sudoers file in a way that it asks for no password while executing the commands as a sudo user. Following is a example on how to make this happen
You can either directly edit the sudoers file or use the visudo to perform the edit , editing through visudo is the recommended way
vi /etc/sudoersOr
visudoAnd add below content and save it
user1 ALL=(ALL) NOPASSWD: ALL
%sudo ALL=(ALL:ALL) NOPASSWD:ALL
From now on we will be able to execute commands as a sudo user without password being asked on a linux machine. Now the below worked without throwing an error even without using the ‘-S’ option
[root@discoveringsystems-centos /]# ssh user1@192.168.94.100 "sudo tcpdump -i ens33 -s 0 -w - -U" | wireshark -k -i -
user1@192.168.94.100's password:
tcpdump: listening on ens33, link-type EN10MB (Ethernet), snapshot length 262144 bytes
How to run remote packet capture using the same command from bash terminal as a root user
While running the similar command as a root user , it is going to be very easy as a root user because of full privilege.
[root@discoveringsystems-centos /]# ssh root@192.168.94.100 "sudo tcpdump -i ens33 -s 0 -w - -U" | wireshark -k -i -
root@192.168.94.100's password:
tcpdump: listening on ens33, link-type EN10MB (Ethernet), snapshot length 262144 bytes
