Table of Contents
- Introduction – Understanding how Arp works
- How arp is used for the Duplicate Address Detection ( DAD )
- Why Gratuitous ARP is used
Introduction – Understanding how arp works
Two linux machines trying to Arp each other to find the destination mac to be used in the ICMP packets While pinging

[root@discoveringsystems-centos /]$ ping 192.168.94.100 -c 1
PING 192.168.94.100 (192.168.94.100) 56(84) bytes of data.
64 bytes from 192.168.94.100: icmp_seq=1 ttl=64 time=0.520 ms
--- 192.168.94.100 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.520/0.520/0.520/0.000 ms
When we tried the above ping example , we were able to see the ping worked. This means that the destination mac address has been resolved through the arp and the reachability test using the ICMP packets ( ping packets ) seems to be fine. I also did a simultaneous tcpdump to view these packet flows.
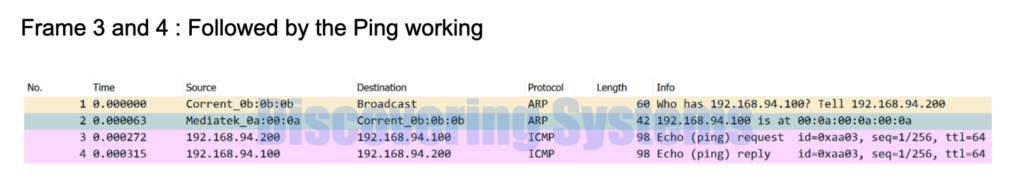
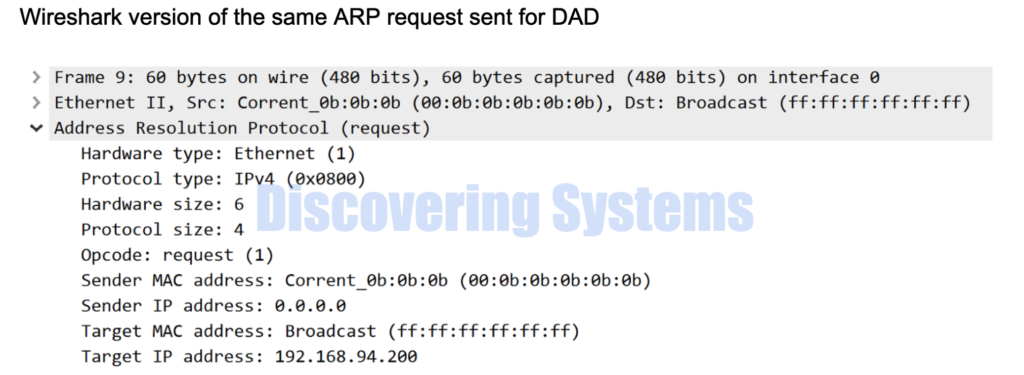
- As soon as the Ping is initiated from the host owning 192.168.94.200 to test reachability for the host 192.168.94.100 , we see an ARP request is generated by the 192.168.94.200 host to resolve the destination mac of the host 192.168.94.100. This arp request packet is a broadcast packet
- We were also able to see an arp response from the host 192.168.94.100 which is a unicast packet destined to the host 192.168.94.200.
- Once the destination macs are resolved using the arp process we were able to see that the ICMP echo request is generated by the host 192.168.94.200 and we got the ICMP echo reply from the host 192.168.94.100 and the ping succeeded
root@DiscoveringSystems-ubuntu:/# tcpdump -nevvi ens38
tcpdump: listening on ens38, link-type EN10MB (Ethernet), snapshot length 262144 bytes
03:17:45.210319 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 tell 192.168.94.200, length 46
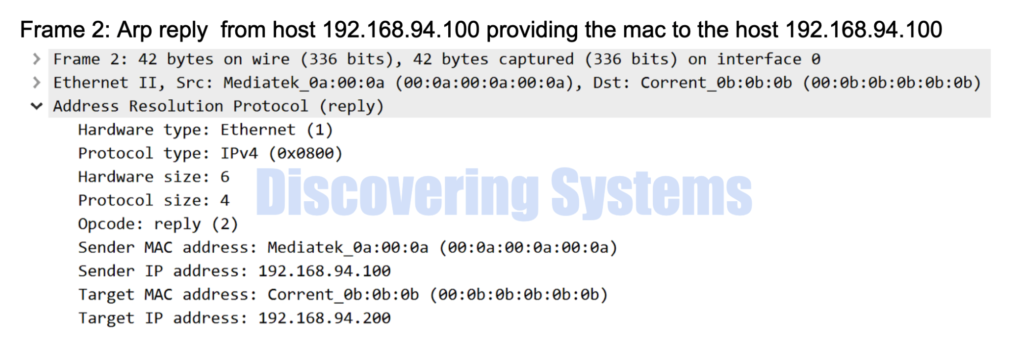
03:17:45.210381 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
03:17:45.210591 00:0b:0b:0b:0b:0b > 00:0a:00:0a:00:0a, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 10530, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.94.200 > 192.168.94.100: ICMP echo request, id 42943, seq 1, length 64
03:17:45.210615 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 12537, offset 0, flags [none], proto ICMP (1), length 84)
192.168.94.100 > 192.168.94.200: ICMP echo reply, id 42943, seq 1, length 64
Same in the wireshark format

How arp is used for the Duplicate Address Detection ( DAD )
To avoid duplicate Ips in the network , as soon as we assign the Ip on the ens33 interface on the Centos machine we were able to see it is using arp packets to do Duplicate address detection to see whether there are any other host connected to the same broadcast domain which has the same IP assigned on it . Technically for the Arp request sent due to DAD we should not get any response , if we get a response there is a Duplicate IP in the same broadcast domain
[root@discoveringsystems-centos /]# ifconfig ens33
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
ether 00:0b:0b:0b:0b:0b txqueuelen 1000 (Ethernet)
RX packets 506 bytes 109098 (106.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 612 bytes 98105 (95.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@discoveringsystems-centos /]# ifconfig ens33 192.168.94.200
root@DiscoveringSystems-ubuntu:/# tcpdump -nevvi ens38
tcpdump: listening on ens38, link-type EN10MB (Ethernet), snapshot length 262144 bytes
03:25:54.702426 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.200 (ff:ff:ff:ff:ff:ff) tell 0.0.0.0, length 46
03:25:55.707178 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.200 (ff:ff:ff:ff:ff:ff) tell 0.0.0.0, length 46
Then I created the duplicate Ip situation and we were able to see there is a response now for the ARP request sent and that is how the duplicate is detected
[root@discoveringsystems-centos /]# ifconfig ens33 192.168.94.100
[root@discoveringsystems-centos /]#
root@DiscoveringSystems-ubuntu:/# tcpdump -nevvi ens38
tcpdump: listening on ens38, link-type EN10MB (Ethernet), snapshot length 262144 bytes
03:26:22.808614 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (ff:ff:ff:ff:ff:ff) tell 0.0.0.0, length 46
03:26:22.808641 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
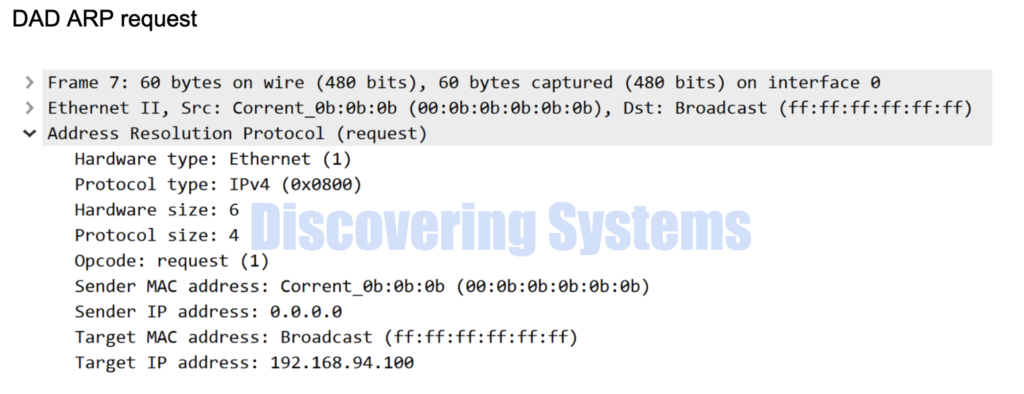
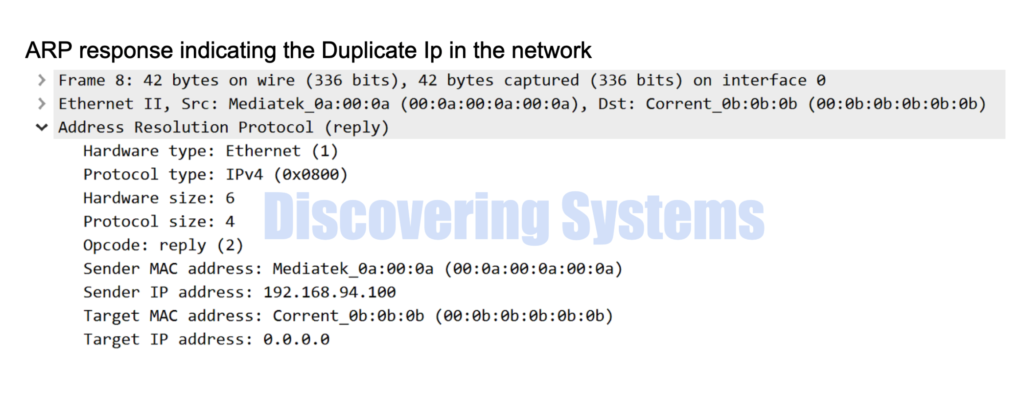
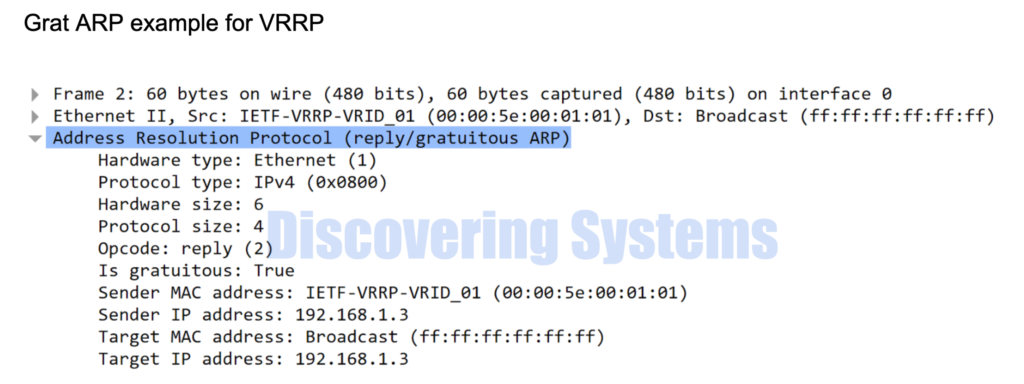
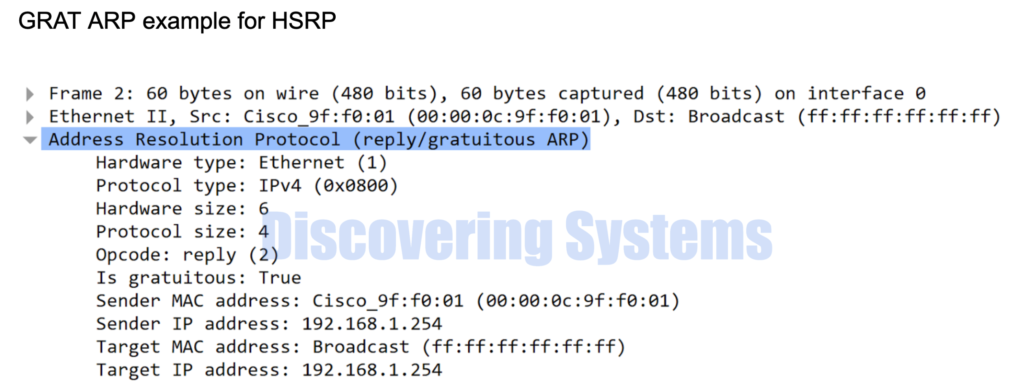
Why Gratuitous ARP is used
This type of ARP is seen in the scenarios of the Virtual Ip Gateways. GARP is sent by the VRRP, HSRP protocol gateways , Arista Ip virtual-router address gateway, etc to make sure the host part of the same network knows the mac address of the gateway.