Table of Contents
- Introduction
- Working of Arping tool
- How to use Arping tool with keep broadcasting option (-b)
- How to restrict number of Arp requests sent out while using arping tool
- How to source arp request from an desired Ip while using arping tool ( -S option )
- How to use Arping tool in answering mode ( option -A )
- How to use Arping tool to send Gratuitous Arp requests ( Option -U)
- How to do Duplicate address detection using the Arping ( Option -D)
- How to use Arping Tool to resolve the Arp and fill the ARP table
Introduction
Wondering how to use the arping tool ? This article covers the use case of the arping tool in detail with examples
Arping is a great tool to check whether we get responses for the ARP requests being sent. Especially when combined with the packet capture utilities it can provide a lot of insights on the networking issues related to resolving of ARP
To view all the options supported by the arping tool we can use the help option
[root@discoveringsystems-centos /]# arping -h
Usage: arping [-fqbDUAV] [-c count] [-w timeout] [-I device] [-s source] destination
-f : quit on first reply
-q : be quiet
-b : keep broadcasting, don't go unicast
-D : duplicate address detection mode
-U : Unsolicited ARP mode, update your neighbours
-A : ARP answer mode, update your neighbours
-V : print version and exit
-c count : how many packets to send
-w timeout : how long to wait for a reply
-I device : which ethernet device to use
-s source : source ip address
destination : ask for what ip address
Working of Arping tool
In this section ,we will look into the working of the Arping tool by using two test cases
- Using the arping tool to send arp request for an Ip which is not present on the network
- Using the arping tool to send arp request for an Ip which is present in the network
First Scenario : Using the arping tool to send arp for an Ip which is not present on the network
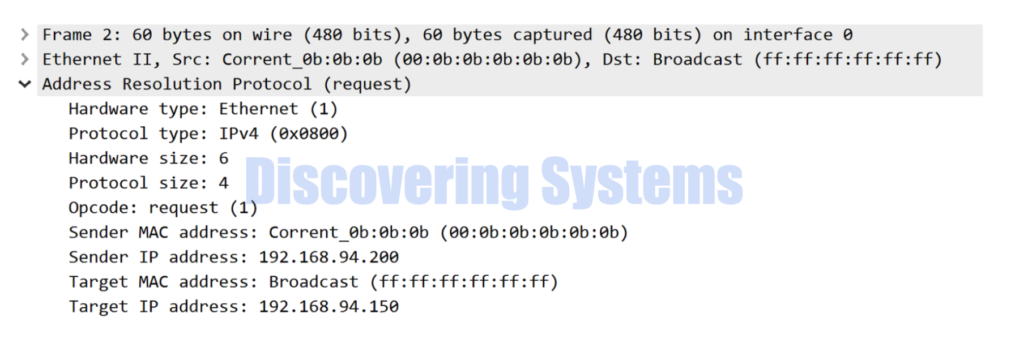
We will be sending an Arp request for an Ip 192.168.94.150 which is not present in the network , to get a glimpse of what happens in the background through the packet captures
The following command example will send a continuous arp request for the IP 192.168.94.150 out of interface ens33 until we stop it using the “ctrl + c “ Sender IP address of the ARP request will be the IP configured on the ens33 interface. We were also able to confirm that we were not receiving the Arp reply for the packets we sent out through the results printed by the Arping tool
[root@discoveringsystems-centos /]# arping -I ens33 192.168.94.150
ARPING 192.168.94.150 from 192.168.94.200 ens33
^CSent 7 probes (7 broadcast(s))
Received 0 response(s)
Here is the packet capture through tcpdump made on the same interface ens33 while using the arping tool and we were able to see ARP request being sent continuously until we stop the arping tool
03:43:12.176759 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
03:43:13.175234 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
03:43:14.173490 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
03:43:15.171922 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
03:43:16.170117 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
03:43:17.168490 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
03:43:18.166777 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
Following is the same arp request packet shown in wireshark format for easy understanding
Second Scenario : Using the arping tool to send an arp for an Ip which is present in the network
In this example we will be using the arping tool on a Ip address(192.168.94.100) which is present on the network and the arp requests are made to be sent out of interface ens33 . We were able to see that the Arp request was sent to 192.168.94.100 and we were getting unicast arp reply packets as response from the Host which owns that IP 192.168.94.100 . This is also continuously sent , until we do “ctrl + c” to stop it . We were also able to confirm that we were receiving the Arp reply for the packets we sent out through the results printed by the Arping tool
[root@discoveringsystems-centos /]# arping -I ens33 192.168.94.100
ARPING 192.168.94.100 from 192.168.94.200 ens33
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 1.219ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.852ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 30.934ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.828ms
^CSent 4 probes (1 broadcast(s))
Received 4 response(s)
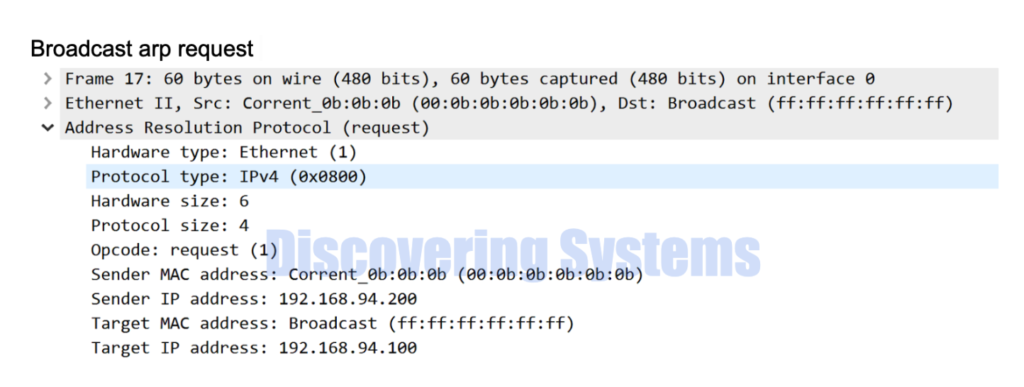
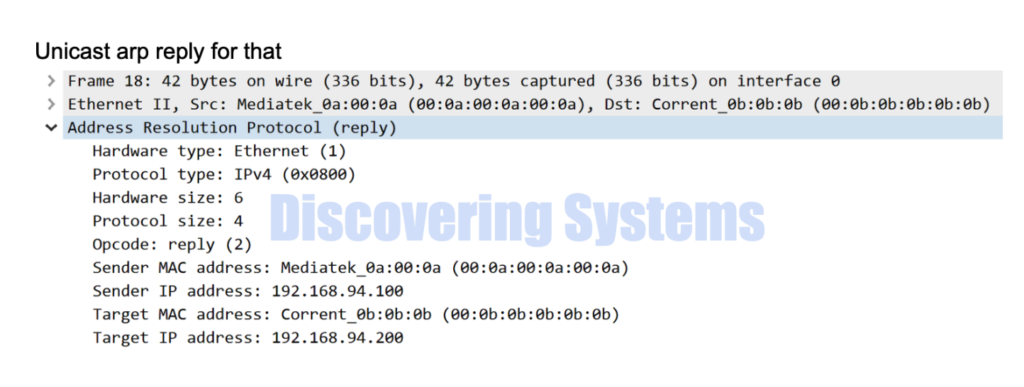
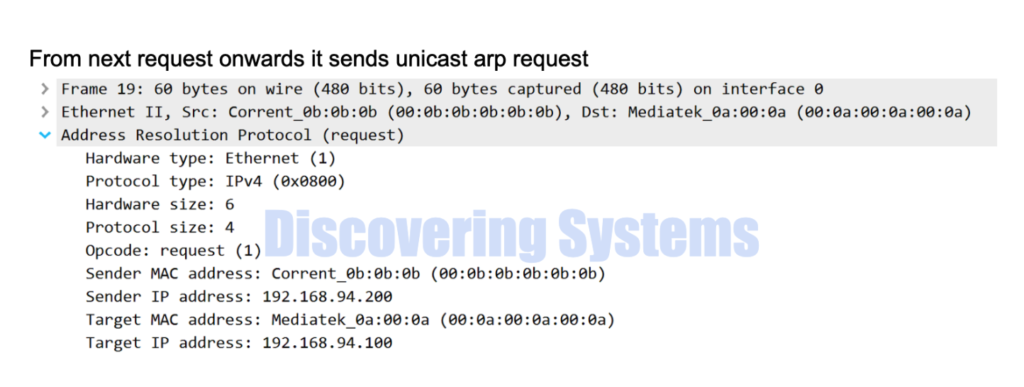
While using the arping tool , we also captured the packets using the tcpdump and was able to see the first arp request is sent as a broadcast packet , and we got a response arp reply for that.
All the following arp requests were switched to unicast arp requests to avoid unnecessary flooding in the network and we also get a arp reply for those packets as well
03:46:03.506273 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
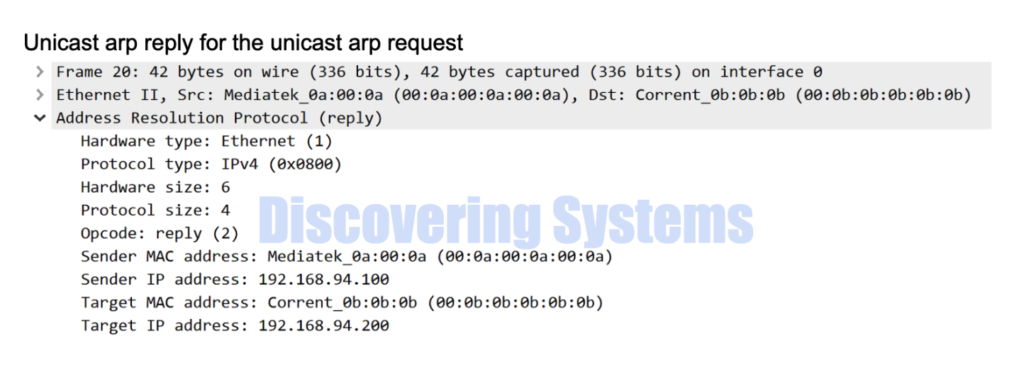
03:46:03.506316 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
03:46:04.506867 00:0b:0b:0b:0b:0b > 00:0a:00:0a:00:0a, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (00:0a:00:0a:00:0a) tell 192.168.94.200, length 46
03:46:04.506886 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
03:46:05.506999 00:0b:0b:0b:0b:0b > 00:0a:00:0a:00:0a, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (00:0a:00:0a:00:0a) tell 192.168.94.200, length 46
03:46:05.507018 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
03:46:06.506801 00:0b:0b:0b:0b:0b > 00:0a:00:0a:00:0a, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (00:0a:00:0a:00:0a) tell 192.168.94.200, length 46
03:46:06.506816 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
The above seen tcpdump packet capture is also shown in wireshark format below for easy understanding
How to use Arping tool with keep broadcasting option (-b)
Lets say if you want to ask arping tool to stick to broadcast arp request always irrespective of whether we received the arp replies or not , we can use the keep broadcasting option (-b)
In the following example , we were sending the arping for the 192.168.94.100 and we can see there is a arp reply received
[root@discoveringsystems-centos /]# arping -b -I ens33 192.168.94.100
ARPING 192.168.94.100 from 192.168.94.200 ens33
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 1.097ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.796ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.835ms
^CSent 3 probes (3 broadcast(s))
Received 3 response(s)
Packet captures using the tcpdump helps us understand destination mac used in the arp request packets to pinpoint the difference when using the keep broadcasting option (-b)
04:35:51.982423 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
04:35:51.982444 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
04:35:52.989812 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
04:35:52.989828 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
04:35:53.995888 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
04:35:53.995906 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
How to restrict number of Arp requests sent out while using arping tool
By default when using the arping tool , it doesn’t stop automatically , however we can force stop it using the “ctrl+c” key combination. Arping tool supports different options to override its default behavior so that we can stop the arp requests being sent out as per our testing needs.
How to use Arping tool with Stop on first reply option (-f )
In this example we will be asking the arping tool to stop after getting the first arp reply. This is possible when using the option -f.
[root@discoveringsystems-centos /]# arping -I ens33 192.168.94.100 -f
ARPING 192.168.94.100 from 192.168.94.200 ens33
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.825ms
Sent 1 probes (1 broadcast(s))
Received 1 response(s)
Below is the packet capture done while we were using the option -f
03:48:45.118455 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
03:48:45.118477 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
How to use Arping Tool with count option (-c)
We can send a number of arp requests and ask the arping tool to stop after that. This is possible using the count option (-c) . In the following example we were asking the arping tool to send only 2 arp requests and we were able to see it got two arp replies as a response
[root@discoveringsystems-centos /]# arping -I ens33 192.168.94.100 -c 2
ARPING 192.168.94.100 from 192.168.94.200 ens33
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.992ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.844ms
Sent 2 probes (1 broadcast(s))
Received 2 response(s)
How to use Arping tool with timeout option (-w)
The timeout option (-w) used along with the arping tool helps to stop the Arp requests automatically after a couple of seconds as per the setting . In the following example we are setting the timeout to be 5 seconds , so after sending a couple of arp requests it times out after 5 seconds and stops automatically.
[root@discoveringsystems-centos /]# arping -w 5 -I ens33 192.168.94.150
ARPING 192.168.94.150 from 192.168.94.200 ens33
Sent 6 probes (6 broadcast(s))
Received 0 response(s)
How to source arp request from an desired Ip while using arping tool ( -S option )
By default the arping tool sources the arp request from the IP and the Mac address owned by the Interface specified , However we can change that behavior and use a different ip in the sender IP address field of the Arp request packet. -S option will help us doing that
In the following example , we were trying to use the IP address 192.168.94.94 as the sender IP in arp request packet instead of the configured Ip address on the interface ens33. Sometimes we might see a error like “ bind: Cannot assign requested address “ in order to solve that you can follow the steps specified below
[root@discoveringsystems-centos /]# arping -s 192.168.94.94 -I ens33 192.168.94.150
bind: Cannot assign requested address
We should be editing the system level setting to allow this through sysctl command. Following is the by default setting which doesn’t allow binding different Ip address
[root@discoveringsystems-centos /]# sysctl net.ipv4.ip_nonlocal_bind
net.ipv4.ip_nonlocal_bind = 0
[root@discoveringsystems-centos /]# arping -s 192.168.94.94 -I ens33 192.168.94.150
bind: Cannot assign requested address
Now we are changing the setting to allow it and further tries on using the (-s ) option with arping tool seems to be working fine
[root@discoveringsystems-centos /]# sysctl -w net.ipv4.ip_nonlocal_bind=1
net.ipv4.ip_nonlocal_bind = 1
[root@discoveringsystems-centos /]# arping -s 192.168.94.94 -I ens33 192.168.94.150
ARPING 192.168.94.150 from 192.168.94.94 ens33
^CSent 14 probes (14 broadcast(s))
Received 0 response(s)
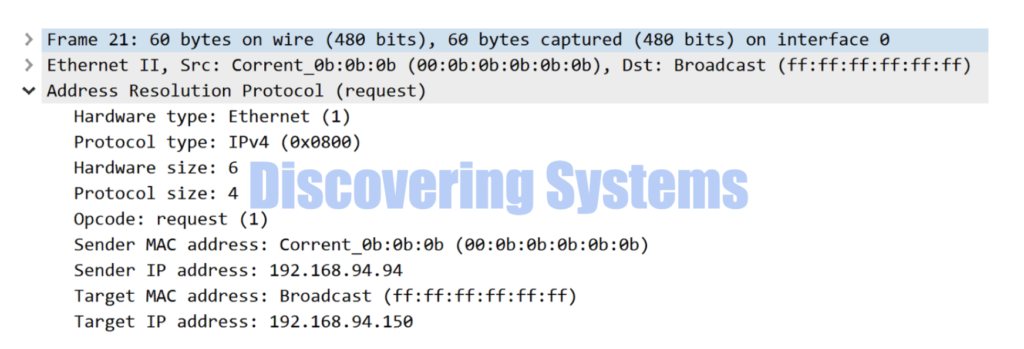
We were also able to confirm that the sender IP field of the arp request now got changed to the new IP address 192.168.94.94. We have both the tcpdump format and wireshark format of the arp request sent out for understanding the change.
03:29:45.197367 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.150 (ff:ff:ff:ff:ff:ff) tell 192.168.94.94, length 46
How to use Arping tool in answering mode ( option -A )
So far in the above sections , we were sending the arp requests and getting arp responses. We can also send the unsolicited arp replies through the Arping tool when Answer mode option (-A) is used . For this to work we should be using the Same Ip address owned by the interface we are referencing with the arping tool. Even this mode is continuous and needs “ctrl + c” to stop it
[root@discoveringsystems-centos /]# arping -A -I ens33 192.168.94.200
ARPING 192.168.94.200 from 192.168.94.200 ens33
^CSent 3 probes (3 broadcast(s))
Received 0 response(s)
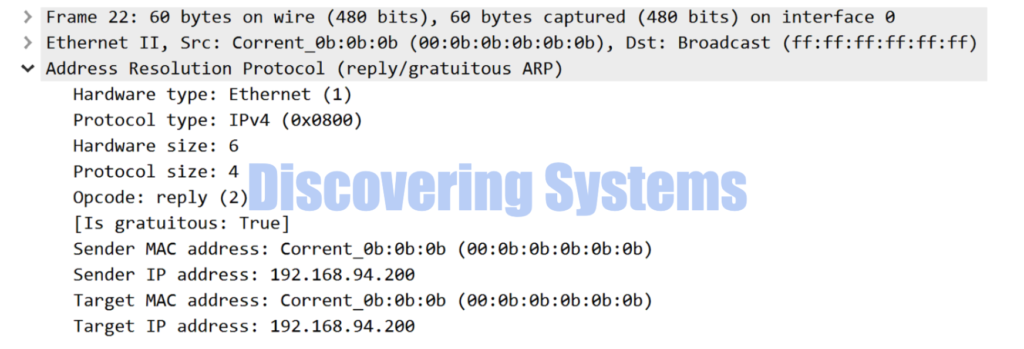
One special thing to note here is the Arp reply packet is sent with the Broadcast mac address , usually the Arp replies are unicast. This is because this mode sends Gratuitous arp reply type packets. This type helps in programming the same Arp entry on all the hosts part of the broadcast domain hence it uses the broadcast mac
Following tcpdump and wireshark example for the same unsolicited arp replies sent which are of Gratuitous type
03:54:11.273785 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.200 is-at 00:0b:0b:0b:0b:0b, length 46
How to use Arping tool to send Gratuitous Arp requests ( Option -U)
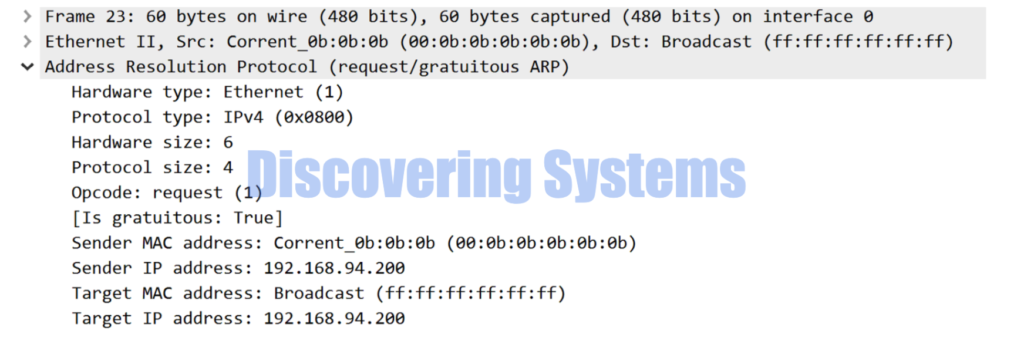
We can use this Unsolicited arp request option ( Option -U) to update the mac address / Ip address owned by the interface we are referencing to arping tool to all the hosts part of the same broadcast domain , but this time just with arp request packets which are of Gratuitous type.
In the following example we were asking the arping tool to send a Gratuitous type arp request with both sender and target Ip to be 192.168.94.200 to update the arp table of other hosts part of the same broadcast domain
[root@discoveringsystems-centos /]# arping -U -I ens33 192.168.94.200
ARPING 192.168.94.200 from 192.168.94.200 ens33
^CSent 4 probes (4 broadcast(s))
Received 0 response(s)
Here is the tcpdump and wireshark example of the same packet being sent out while using the above example command
03:59:04.616186 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.200 (ff:ff:ff:ff:ff:ff) tell 192.168.94.200, length 46
How to do Duplicate address detection using the Arping ( Option -D)
Many systems support this Duplicate address detection, whenever a new Ip address is assigned to an interface it sends an ARP request requesting the Mac address for the same IP which is assigned , if we get an ARP response for that then we can detect there is a duplicate IP address configured. In this section we will discuss how the Arping tool can be used to detect the duplicate IP address in the network.
How to use option -D with arping tool for a non-duplicate IP scenario
In the following example we are asking the arping tool send the Arp requests from the sender IP as 0.0.0.0 and the target ip as the Ip we request it to use 192.168.94.200 along with the option -D and interface is set to be ens33 through which the packets will be sent out. Ip address 192.168.94.200 is the IP owned by ens33 and there is no Duplicate Ip in the network so we didn’t get any response and the Arping continued to send the packets until we stopped it manually using the Ctrl + c
[root@discoveringsystems-centos /]# arping -D -I ens33 192.168.94.200
ARPING 192.168.94.200 from 0.0.0.0 ens33
^CSent 10 probes (10 broadcast(s))
Received 0 response(s)
Here is the packet capture made using tcpdump and wireshark during the same time when we used the above commands
04:08:31.359254 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.200 (ff:ff:ff:ff:ff:ff) tell 0.0.0.0, length 46
04:08:32.362580 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.200 (ff:ff:ff:ff:ff:ff) tell 0.0.0.0, length 46
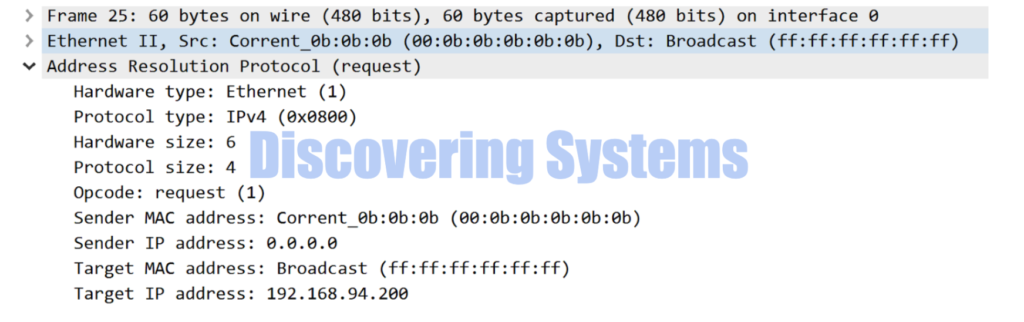
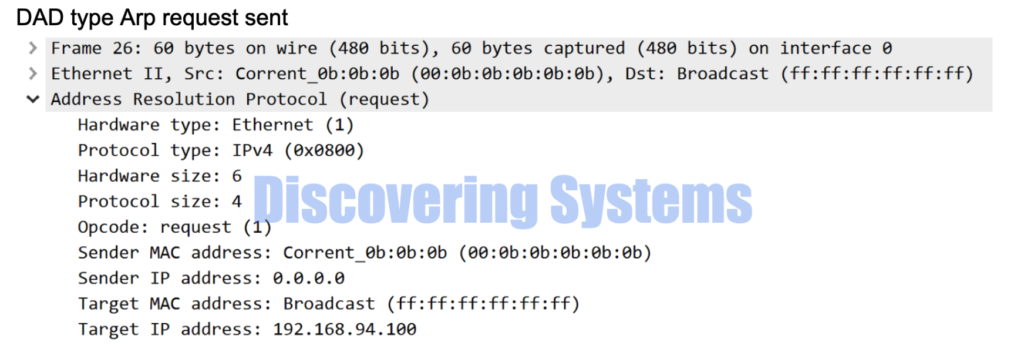
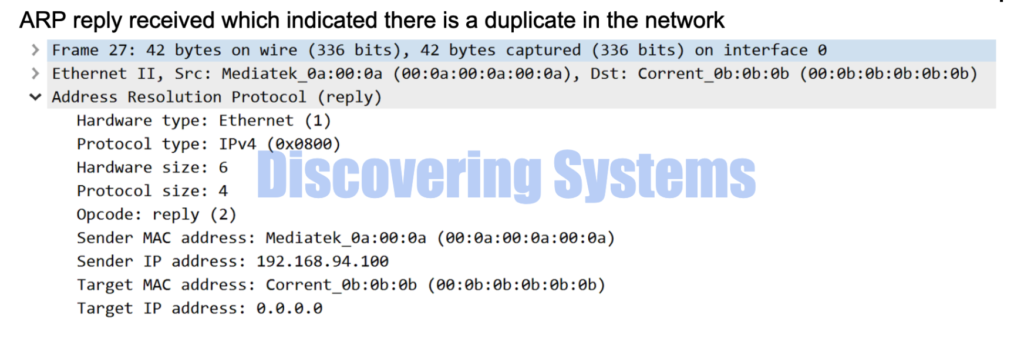
How to using option -D with arping tool for a duplicate IP scenario
Now we are sending the DAD ( Duplicate Address detection ) type ARP for an Ip which we know that there is a duplicate present and we see that arping tool immediately stopped telling us there is a duplicate
[root@discoveringsystems-centos /]# arping -D -I ens33 192.168.94.100
ARPING 192.168.94.100 from 0.0.0.0 ens33
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 1.259ms
Sent 1 probes (1 broadcast(s))
Received 1 response(s)
Here is the packet capture made using tcpdump and wireshark during the same time when we used the above commands
04:13:38.373304 00:0b:0b:0b:0b:0b > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.94.100 (ff:ff:ff:ff:ff:ff) tell 0.0.0.0, length 46
04:13:38.373318 00:0a:00:0a:00:0a > 00:0b:0b:0b:0b:0b, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 192.168.94.100 is-at 00:0a:00:0a:00:0a, length 28
How to use Arping Tool to resolve the Arp and fill the ARP table
Arping doesn’t help to fill the local arp table by default , even though it gets the arp reply , we need to use utilities such as ping to send a legit arp instead of testing arp probes to resolve it
For example , we see there is a ARP entry present for the 192.64.94.100 in the ARP table and we are removing it and trying to use arping tool to resolve it again , we won’t see the ARP getting resolved in the ARP table for that IP even though the Arping tool got responses. However there is a way to fix this which will be discussed in the next section
[root@discoveringsystems-centos /]# arp -a
? (192.168.94.100) at 00:0a:00:0a:00:0a [ether] on ens33
We deleted the entry
[root@discoveringsystems-centos /]# arp -d 192.168.94.100
Then trying arping for the same IP address and we got responses as well
[root@discoveringsystems-centos /]# arping -I ens33 192.168.94.100
ARPING 192.168.94.100 from 192.168.94.200 ens33
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.759ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.789ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.844ms
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 0.828ms
^CSent 4 probes (1 broadcast(s))
Received 4 response(s)
Still the arp is not resolved in the table
[root@discoveringsystems-centos /]# arp -a
< no entry present >
Now let’s fix this
We can see that there is a default setting which stops this from happening , so we need to edit the settings in order for making arping tool help resolve the ARP entries in the ARP table
[root@discoveringsystems-centos /]# sysctl net.ipv4.conf.all.arp_accept
net.ipv4.conf.all.arp_accept = 0
Now editing the settings in order to allow learning the ARP table entries even though it is unsolicited type
[root@discoveringsystems-centos /]# sysctl -w net.ipv4.conf.all.arp_accept=1
net.ipv4.conf.all.arp_accept = 1
Now using arping tool again to resolve the entries and this time it worked
[root@discoveringsystems-centos /]# arping -f -I ens33 192.168.94.100
ARPING 192.168.94.100 from 192.168.94.200 ens33
Unicast reply from 192.168.94.100 [00:0A:00:0A:00:0A] 1.171ms
Sent 1 probes (1 broadcast(s))
Received 1 response(s)
[root@discoveringsystems-centos /]# arp -a
? (192.168.94.100) at 00:0a:00:0a:00:0a [ether] on ens33
